Failed To Start Openssh Server Key Generation
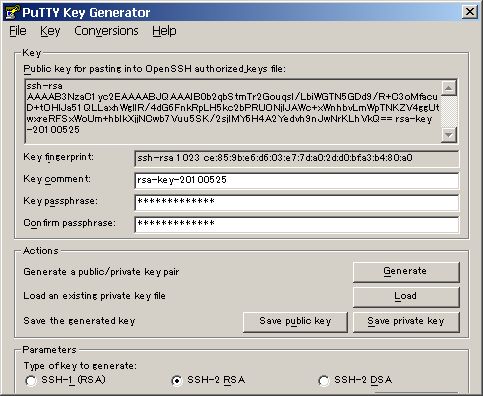
Openssh Server Windows
Failed To Start Openssh Server Key Generation
Ssh-keygen -f /tatu-key-ecdsa -t ecdsa -b 521 Copying the Public Key to the Server. To use public key authentication, the public key must be copied to a server and installed in an authorizedkeys file. This can be conveniently done using the ssh-copy-id tool. Like this: ssh-copy-id -i /.ssh/tatu-key-ecdsa user@host. When booting the F-25 Beta RC images I see 2 errors regarding OpenSSH key generation from console. Starting OpenSSH ecdsa Server Key Generation. 0;1;31mFAILED 0m Failed to start OpenSSH ed25519 Server Key Generation. See 'systemctl status sshd-keygen@ed25519.service' for details. 0;1;31mFAILED 0m Failed to start OpenSSH ecdsa. For more information on the key generation options, see the ssh-keygen2 man page (Appendix ssh-keygen2). Restart the server as instructed in Section Restarting sshd2. Using an OpenSSH Server Host Key. SSH Tectia Server for IBM z/OS can use a key created with OpenSSH as the server host key. Ssh-keygen -f /tatu-key-ecdsa -t ecdsa -b 521 Copying the Public Key to the Server. To use public key authentication, the public key must be copied to a server and installed in an authorizedkeys file. This can be conveniently done using the ssh-copy-id tool. Like this: ssh-copy-id -i /.ssh/tatu-key-ecdsa user@host.
|