Ssh Key Generation In Centos
Reading Time: 3 minutes This guide will walk you through the steps to create a Certificate Signing Request, (CSR for short.) SSL certificates are the industry-standard means of securing web traffic to and from your server, and the first step to getting your own SSL is to generate a CSR. This key size will be 4096 bit. 4096 bit keys are a lot more secure than 2048 or 1024 bit keys. If we are not transferring big data we can use 4096 bit keys without a performance problem. We will use -b option in order to specify bit size to the ssh-keygen.
Ssh is secure protocol used to manage remote systems like Linux, BSD, UNIX, network devices event windows operating systems. The traffic between systems are encrypted. Ssh uses asymmetric keys in order to encrypt and made traffic invisible to the others those resides between systems in the network. The encryption power comes from key bit size or length. In this tutorial we will look how to create 4096 bit keys.
Ssh Key Generation Centos
In this example we will generate very secure key. This key size will be 4096 bit. 4096 bit keys are a lot more secure than 2048 or 1024 bit keys. If we are not transferring big data we can use 4096 bit keys without a performance problem. We will use -b option in order to specify bit size to the ssh-keygen .
RSA is very old and popular asymmetric encryption algorithm. It is used most of the systems by default. There are some alternatives to RSA like DSA . We can not generate 4096 bit DSA keys because it algorithm do not supports.
The default key size for the ssh-keygen is 2048 bit. We can also specify explicitly the size of the key like below.
The less secure key size is 1024 bit. We do not recommend usage of this size of keys but in some situations like old systems we may need this size of keys. Here how we can generate 1024 bit key with ssh-keygen .
With a secure shell (SSH) key pair, you can create virtual machines (VMs) in Azure that use SSH keys for authentication, eliminating the need for passwords to sign in. This article shows you how to quickly generate and use an SSH public-private key file pair for Linux VMs. You can complete these steps with the Azure Cloud Shell, a macOS or Linux host, the Windows Subsystem for Linux, and other tools that support OpenSSH.
Ssh Key Generation In Centos 10
Note
VMs created using SSH keys are by default configured with passwords disabled, which greatly increases the difficulty of brute-force guessing attacks.
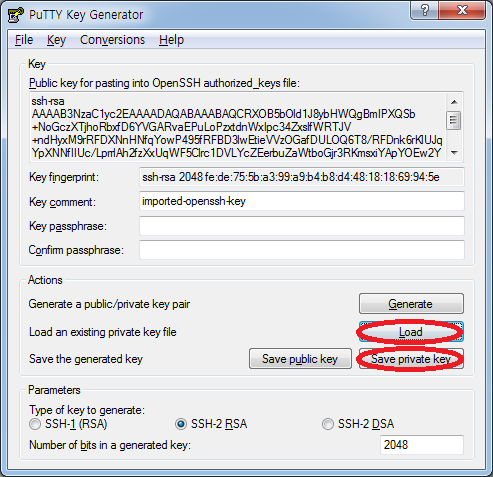
For more background and examples, see Detailed steps to create SSH key pairs.
For additional ways to generate and use SSH keys on a Windows computer, see How to use SSH keys with Windows on Azure.
Supported SSH key formats
Azure currently supports SSH protocol 2 (SSH-2) RSA public-private key pairs with a minimum length of 2048 bits. Other key formats such as ED25519 and ECDSA are not supported.
Create an SSH key pair
Use the ssh-keygen command to generate SSH public and private key files. By default, these files are created in the ~/.ssh directory. You can specify a different location, and an optional password (passphrase) to access the private key file. If an SSH key pair with the same name exists in the given location, those files are overwritten.
The following command creates an SSH key pair using RSA encryption and a bit length of 4096:
If you use the Azure CLI to create your VM with the az vm create command, you can optionally generate SSH public and private key files using the --generate-ssh-keys option. The key files are stored in the ~/.ssh directory unless specified otherwise with the --ssh-dest-key-path option. The --generate-ssh-keys option will not overwrite existing key files, instead returning an error. In the following command, replace VMname and RGname with your own values:
Provide an SSH public key when deploying a VM
To create a Linux VM that uses SSH keys for authentication, specify your SSH public key when creating the VM using the Azure portal, Azure CLI, Azure Resource Manager templates, or other methods:
Centos Ssh Authorized Keys
If you're not familiar with the format of an SSH public key, you can display your public key with the following cat command, replacing ~/.ssh/id_rsa.pub with the path and filename of your own public key file if needed:
A typical public key value looks like this example: Git ssh generate public key.
If you copy and paste the contents of the public key file to use in the Azure portal or a Resource Manager template, make sure you don't copy any trailing whitespace. To copy a public key in macOS, you can pipe the public key file to pbcopy. Similarly in Linux, you can pipe the public key file to programs such as xclip.
The public key that you place on your Linux VM in Azure is by default stored in ~/.ssh/id_rsa.pub, unless you specified a different location when you created the key pair. To use the Azure CLI 2.0 to create your VM with an existing public key, specify the value and optionally the location of this public key using the az vm create command with the --ssh-key-values option. In the following command, replace VMname, RGname, and keyFile with your own values:
If you want to use multiple SSH keys with your VM, you can enter them in a space-separated list, like this --ssh-key-values sshkey-desktop.pub sshkey-laptop.pub.
SSH into your VM
With the public key deployed on your Azure VM, and the private key on your local system, SSH into your VM using the IP address or DNS name of your VM. In the following command, replace azureuser and myvm.westus.cloudapp.azure.com with the administrator user name and the fully qualified domain name (or IP address):
If you specified a passphrase when you created your key pair, enter that passphrase when prompted during the login process. The VM is added to your ~/.ssh/known_hosts file, and you won't be asked to connect again until either the public key on your Azure VM changes or the server name is removed from ~/.ssh/known_hosts.
If the VM is using the just-in-time access policy, you need to request access before you can connect to the VM. For more information about the just-in-time policy, see Manage virtual machine access using the just in time policy.
Next steps
For more information on working with SSH key pairs, see Detailed steps to create and manage SSH key pairs.
If you have difficulties with SSH connections to Azure VMs, see Troubleshoot SSH connections to an Azure Linux VM.